From the perimeter to the core, detection technologies include:
Network Monitor visibility can be placed at multiple points in a network. The traditional configuration is at an organizations internet egress point. This is where a span or mirror port is provisioned on a switch or tap and positioned before NAT occurs so that the source IP is preserved. Another configuration for Network Monitor is placement between inter-office traffic or between two branch offices |man in the middle|. This placement can be due to compliance and data governance efforts. Weaknesses in Network Monitor is not having visibility concerning SSL/TLS traffic and not having the capability to take action or prevent the web transactions from traversing out the corporate network.
However, there have been two new integrations for Network Monitor that solves the encrypted traffic dilemma:
1-Using the Blue Coat SSL Visibility Appliance
“The Blue Coat SSL Visibility Appliance is a dedicated network appliance designed to decrypt SSL traffic and provides a clear-text stream of the session using a TAP port. Symantec Data Loss Prevention Network Monitor can receive and monitor the clear-text packets from the SSL Visibility Appliance for all protocols that Network Monitor currently supports, such as SMTP over TLS, FTPS, and HTTPS. Symantec has certified Network Monitor with the Blue Coat SSL Visibility Appliance to enable monitoring of SSL traffic passing out of the corporate network. The integration of Network Monitor with the Blue Coat SSL Visibility Appliance is passive-inline. The appliance serves as a “bump in the wire” device between a user’s managed enterprise computer and the website that the user is accessing.”
https://support.symantec.com/en_US/article.TECH231642.html
2-Using Palo Alto Networks Next-Generation Firewall SSL decryption feature to monitor decrypted SSL/TLS traffic
“The Palo Alto Networks next-generation firewalls are dedicated network appliances that contain a decryption port monitoring feature designed to decrypt SSL/TLS traffic. The SSL/TLS decryption feature provides a clear-text stream to Symantec Data Loss Prevention Network Monitor. Network Monitor receives and monitors the clear-text packets from the Palo Alto Networks next-generation firewall for all protocols that Network Monitor currently supports, such as SMTP over TLS, FTPS, and HTTPS. The integration of Network Monitor with the next-generation firewall's SSL/TLS decryption feature is passive-inline. The appliance serves as a “bump in the wire” device between a user’s managed enterprise computer and the websites that a user accesses.”
https://support.symantec.com/en_US/article.TECH234916.html
Based on these enhancements, existing DLP customers should consider re-architecting their existing Symantec DLP Network Monitor|s| to take advantage of these noteworthy integrations.
Another layer of protection is Network Prevent for Web (NPW) detection technology. NPW integrates with Enterprise Web Proxy solutions that are Internet Content Adaptation Protocol |ICAP| compliant. Examples are BlueCoat ProxySG and Cisco IronPort WSA. Additionally, NPW can invoke actions to be taken on the web post transactions. A verdict is sent to the Web proxy solution to block, allow or redact the web transaction which is compared against DLP rules.
Lastly, is the DLP Endpoint Agent. At the application layer and often codified as “data in use” is where the DLP Endpoint agent operates on the end user PCs. When installed, the Endpoint Agent can monitor many channels or vectors for exfiltration of sensitive data on the Endpoint. For the intent and purpose of this article, the Web channel will be highlighted. As of DLP version 14.6, supported Web communication channels include:
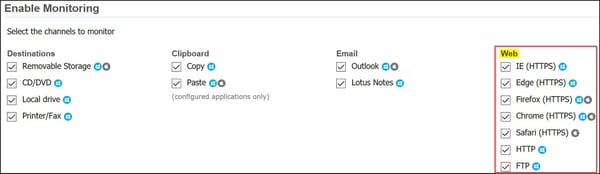
Image captured from Symantec DLP v.14.6 |System>Agents>Agent_Configuration|
Note that the DLP MAC agent supports Firefox, Chrome, and Safari (HTTPS). Also, Endpoint Prevent response rules can take action by blocking, notifying, and the “user cancel” patience pop-up dialog box (time-out). By using the response rule block action, the transmission never makes it to the Network layer, so in other words, it is stopped dead in its track on the Endpoint device. I favor, Endpoint Prevent since it provides a wide array of coverage on the endpoint and can present a variety of Prevent Responses to terminate sensitive data transmission while educating the end user.
Based on an organizations risk appetite, these technologies can be implemented using a risk-based approach, or the suite of detection technologies can be implemented in a systematic deployment methodology over time. Network Monitor - at the edge, Network Prevent Web - at the DMZ integrating with a Web Proxy solution and Endpoint Prevent - at the core leveraging the DLP Endpoint Agent.
These Stories on Productive IT Management