
Today we wanted to talk about how ITS Partners can simplify application creation within your Configuration Manager environment.
If you've ever created an application in Configuration Manager, you know that it can be a time consuming or tedious task. Especially if you are creating an application from a non-MSI installer file. MSI installers make things very simple when dealing with Configuration Manager applications. You go through the Application Creation wizard, you point to the MSI file, and Configuration Manager builds your application for you. You may have to go back and change a few settings, but all of the important details are defined for you.These details include, but are not limited to things like:
This is great when you're creating MSI based applications, but this process becomes a lot more "hands-on" when you have to create an application from non-MSI media. This includes executables, scripts, and other non-standard installers. When you try to build an application using these media types, you have to manually identify the items like the install string and the detection check. Again, this is not exactly a complicated thing to accomplish, but it can be very daunting; especially when you don't already know your detection method. For those who are not aware, detection methods are "rules" that you define within an application that the application uses to determine whether or not it installed properly. These detection methods can check for registry keys, or files and/or file versions, as well as the option to create script based detection checks. Gathering these details can be a bit tricky depending on the application. If it is not a common application, an administrator has to manually install the software, and manually go determine a detection method. This detection method then needs to be validated against the installation as well as the removal and reinstallation of an application in Configuration Manager to determine that a valid detection method was utilized. One common concern with randomly selecting a registry entry to key off of is the possibility that vendors do not change or modify certain registry keys between different versions of an application. Another concern is that registry entries may not be thoroughly cleaned out when an application is removed. This can lead to inaccurate installation results when an application is delivered to or removed from a device.
"What is it that makes ITS Partners so different from everyone else when it comes to creating Configuration Manager applications?" The answer: We automate the mundane!
That means we take the tedious and manually intensive tasks, like finding detection methods for 100's of pieces of software to create Configuration Manager applications. But how could we accomplish something like that? How in the world do we automate something that requires so much manual user interaction? We have a cool whitepaper if you want to read more.
To be quite honest, it isn't all that hard to create some form of automation around building applications and deployment types in Configuration Manager. The part that is a bit more complicated is providing the application specific data to the automation tool that is building these applications.
ITS Partners has some automation that greatly simplifies the process of creating applications in Configuration Manager. This process can be used for net-new applications, or package-to-application migrations, or even a migration of software deliverables from other systems management tools. So how does this all work?
ITS Partners has a growing database containing details about applications including the application hash, the installation strings and the detection methods.
We define a client data matrix containing the basic application details for the applications that will be created. This includes things like the application name, the installation string, and the package source path.
ITS Partners automates the creation of the applications in Configuration Manager utilizing the database and data matrix. This process will create "filler" detection methods. This means we define a "known, bad" detection method into the application.
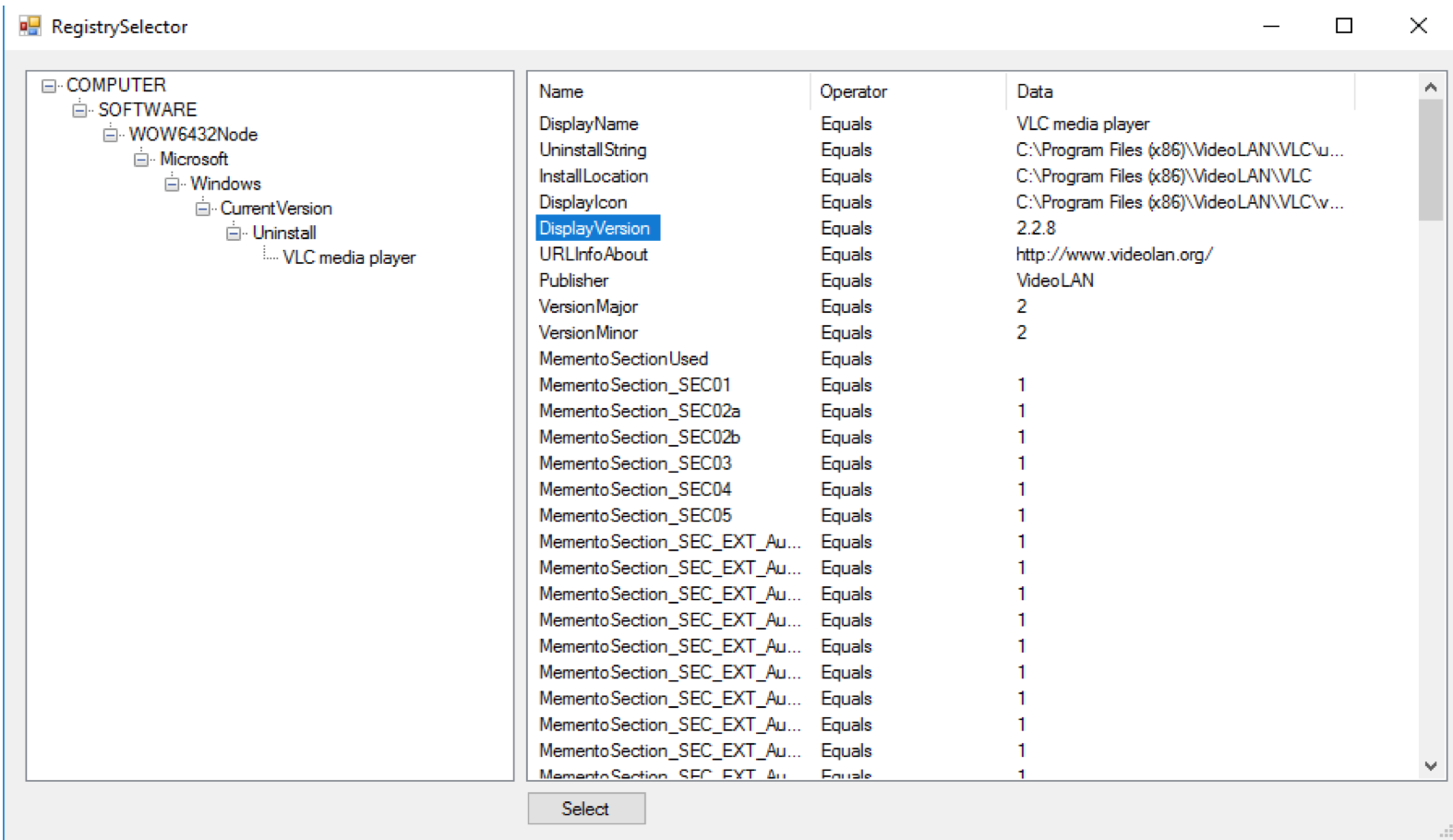
Screenshot of registry selection option for applications that need manual selection
Now that we have discussed the process, let's talk a little bit about the tools we use to accomplish this. These utilities are created in and with Microsoft Azure cloud services using Azure Functions. Using Azure Functions allows us to:
We took this approach because this allowed us to build a scalable and secure solution for "large-scale" application packaging projects. This also allows for the ITS engineer to run multiple processes in parallel with each other.
Although this process does still require some manual efforts, a good majority of the tedious and mundane work has been automated. ITS Partners has created 100's of applications in a single day by utilizing this utility, and we would love to help you accomplish those same results.
Post co-authored by Adam Eaddy, Consulting Architect and Cris Weber, Lead Development architect.
These Stories on Microsoft